Policy Foundation and Management
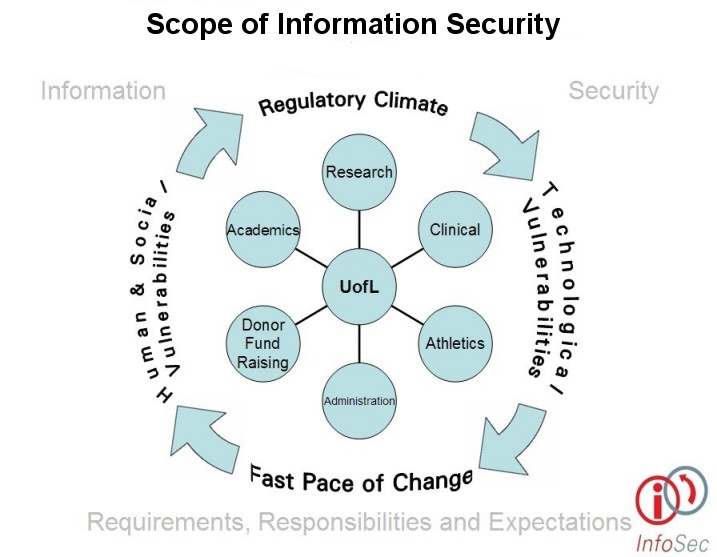
The university's Information Security Policies and Standards were developed as a common foundation for information security outlook, approach and practice. Primary consideration was given to the following objectives:
- Help the university to focus on its core missions of research and academic excellence by lowering the risk of security incidents which could distract from these missions.
- Define a compliance posture relative to information security statutes, regulations, contracts and good practice without duplication of effort. (One set of policies and standards designed to address all information security compliance objectives instead of one for HIPAA, one for FERPA, one for PCI, etc.)
- An approach that is, where possible, technology neutral that allows for some variation given legitimate requirements so long as the risk is explicitly defined and accepted by a level of directly responsible management appropriate to the risk being assumed.
- An approach that accounts for the dynamic environment we are in today, an environment of changing statutory and regulatory expectations and changing technology where awareness is an integral part of everyone's job
What is a policy?
The definitions of what is a policy, what is a standard and what is a procedure also had to be understood. Without this understanding of related but distinct terms, policies tend to become too detailed and take on the characteristics of standards or procedures.
For the purposes of the university's Information Security Policies and Standards (as well as related procedures), the following definitions are used:
- Policy - High level requirement statement or paragraph about a type of technology or behavior in the IT environment.
- Standard - A required approach for conducting an activity or using technology and/or descriptive requirements for a behavior based policy.
- Procedures - Clear steps to follow to accomplish specific tasks or behave in certain ways. Procedures should support organization, contractual, regulatory and/or statutory obligations and requirements
Once the strategic positioning of the Information Security Policies and Standards was determined, a review and comment process was initiated so university constituents would have an opportunity to voice suggestions and concerns.